- Latest report shows cryptomining is now the world’s second-most popular malware
- It can cause mobile phones to overheat and explode
- Has your computer’s fan been unusually noisy lately?
Good news – virtually all traditional types of malware declined in the last few months.
Not so good – mainly because hackers are more interested in using your computer to help them mine cryptocurrencies.
It’s likely you, or your employer, aren’t even aware it’s happening. Malware miners latch onto your PC and add its processing power to their efforts to stock up on Monero, ByteCoin, AEON, or any one of a number of the new breed of cryptos which don’t need a mining rig the size of a city block to get meaningful returns.
Adding to the attraction is a misguided sense that it just doesn’t feel as sinister as someone stealing your banking details or holding your adulterous website membership to ransom.
There’s even been recent moves by major media companies offering ad-free services in exchange for your PC’s power. Some refer to it as “ethical cryptomining”.
But according to the latest quarterly report on cybercrime tactics and techniques by security software provider Malwarebytes, “malicious cryptomining” has come from nowhere in the past few months to now being the second-most popular form of cybercrime, “nipping at the heels” of adware.
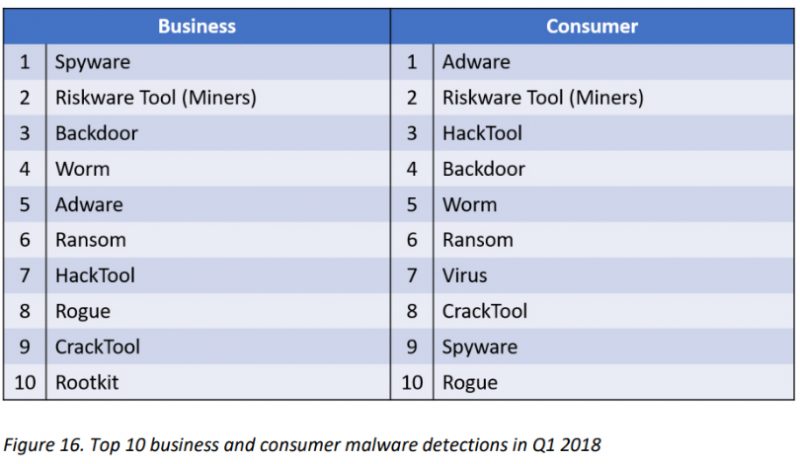
Currently, adware still stands as the number one threat for consumers, while spyware is the biggest threat to businesses.
Ransomware – where victims are asked to pay up, usually in bitcoin – is up for businesses by 28%, but consumer detections fell, dragging it down to sixth spot overall. A new development saw GandCrab become the first ransomware to ask victims to pay up in a crypto other than bitcoin.
But why risk jail time by demanding a couple of hundred dollars in bitcoin when you can just mine it, with a little bit of unsolicited help?
While virtually all other malware is on the decline, cryptomining is now the number two threat to consumers and businesses.
Android owners in particular have been targeted, with Malwarebytes finding a 4000% increase for the quarter. Mac user detections were lower, but they rose 74% in March.
“Cryptocurrency mining is such a lucrative business that malware creators and distributors all over the world are drawn to it like moths to a flame,” the report said.
“We’ve seen malicious cryptomining on a grand scale this quarter—on all platforms, devices, operating systems, and in all browsers.
“Macs and mobile devices are not exempt; criminals have even used the cryptocurrency craze for social engineering purposes.”
The most popular places for criminals to infect are servers. Windows servers, Oracle servers, and recently Amazon servers have all been infected with cryptocurrency miners. Infect the server and those using them – notably, Amazon’s cloud-based AWS service – could suddenly unwittingly be hosting a miner on their website.
A recent example was found lurking on the LA Times website. And Australian government websites. And websites run by the UK’s National Health System, Student Loans Company and Northern Powergrid.
But why target Android users? The computing power is negligible, but Malwarebytes says it’s easy to “up the ante” by adding miners to already malicious apps.
A recent version, a miner added to the Loapi Trojan, pushed devices to the point that they “overheated due to the strain on the processor, their batteries bulged, and ultimately, they suffered an untimely end”.
That sounds… familiar.
But the biggest player is CoinHive. It’s only been truly active since September 2017, when it announced an API that could mine Monero directly from within a web browser.
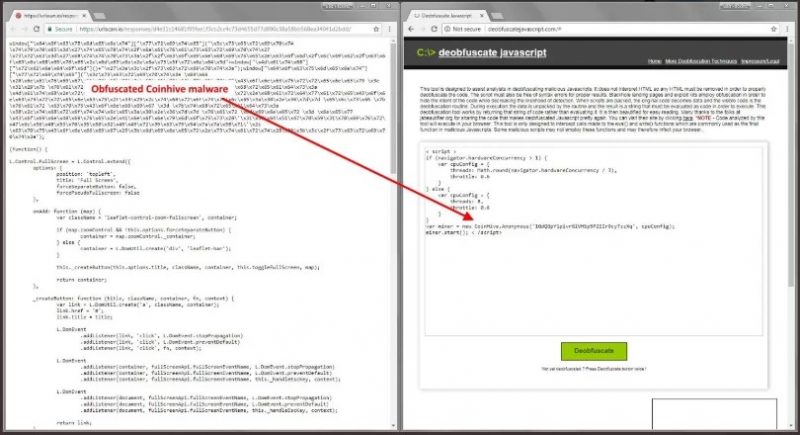
It was launched with good intent, but “due to several oversights, the technology was almost instantly abused,” Malwarebytes reported.
The beauty of CoinHive is, it’s hard to spot because it doesn’t slow down your computer a whole lot. It’s used in “drive-by cryptomining”.
Drive-by cryptomining is website specific and doesn’t require infecting a machine. Open the modified webpage – such as the LA Times page noted above – and your PC starts mining Monero for someone else. Close the tab or browse away from it, and the mining stops.
You probably just get annoyed at the tardy website.
But here’s a neat trick drive-by miners are using – pop-unders.
You won’t see a pop-under tab because it’s like a pop-up tab, except it opens under your taskbar. Even though you think you’ve left the affected website, the tab keeps chugging away.
You probably left one open all last night.
CoinHive itself takes a 30% commission from all mining earnings. The fact that knowledge is so openly discussed, and there’s been no notable reparation against CoinHive, is probably a large part of why cryptomining is the rising malware star of 2018.
In CoinHive’s defence, it did release another API that requires users to opt in – the “ethical” cryptominer. But MalwareBytes’ research shows that its was used about 30,000 times a day compared to the silent API at 3 million times per day.
The new wave is already coming – Coin Have and CryptoLoot are number two and three. Coin Have takes 20 per cent, but CryptoLoot claims to pay out 88%.
Cryptominers are actually advertising better rates for letting other people steal your computing power. They also promote their ability to bypass their biggest threat – ad blockers.
But here’s a tip for spotting it on your PC at least – that moment when its fan is going berserk.
In January, one miner even went to the length of letting Android phone users know they were being mined, which was polite. Look at the CPU usage, off the scale:
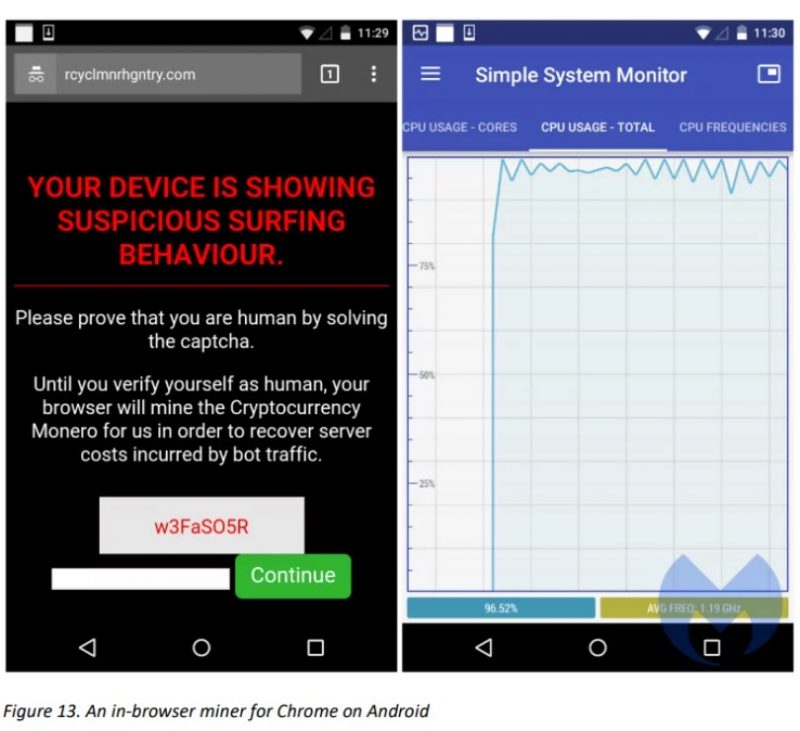
You could opt out by “verifying yourself as human”.
Malwarebytes says there’s no reason to expect the rise in cryptomining to continue in 2018, especially given the value of cryptocurrencies, despite their recent dips.
The new frontier, it says, could be Internet of Things devices. How much attention are you paying to what your smart fridge is doing right now?
“While malicious cryptomining appears to be far less dangerous to the user than other forms of malware, such as ransomware, its effects should not be undermined,” Malwarebytes says.
“Indeed, unmanaged miners could seriously disrupt business or infrastructure-critical processes by overloading systems to the point where they become unresponsive and shut down.
“Under the disguise of a financially-motivated attack, this could be the perfect alibi for advanced threat actors.”
How to spot it
- Basically, your computer’s fan is going berserk. Check your CPU usage (Task Manager, Windows; Activity Monitor, Mac) and look for spikes
How to stop it
- If you’re a business, Malwarebytes has just released its new Endpoint Protection and Response solution.
- Antivirus software. The first go-to for anything like this. If you’re not convinced by your built-in protection, try Kaspersky or BitDefender.
- Adblockers help. AdBlock Plus and AdGuard offer to scan sites for CoinHive. No Coin and Miner Block are also handy Chrome extensions.
- And if you see an unusual program taking up your CPU usage, simply stop it, then scan for a virus.











