Internet users around the world, but mostly in the US, reported that some top websites were not loading on Friday morning.
The affected sites include Amazon, Twitter, Netflix, Etsy, Github, and Spotify.
It was mostly resolved at 9:20 a.m. ET, but at 12:07 p.m. ET, the issue started to crop up again, according to Dyn, one of the companies at the center of the apparent cyber attack.
At 4:16 p.m. ET, Dyn said that it was facing a third wave of attacks, CNBC reported.
Around 6:20 p.m. ET, Dyn said that the incident had been resolved, according to a status update on its website.
The issue appears to have something to do with DNS hosts - in particular, Dyn, one of the biggest DNS companies.
Domain Name Servers are a core part of the internet's backbone. They translate what you type into your browser -www.businessinsider.com, for example - into IP addresses that computers can understand.
Dyn said on Friday that it suffered a DDoS attack, or a distributed denial of service. That basically means hackers are overwhelming Dyn's servers with useless data and repeated load requests, preventing useful data - the Twitter IP address, for example - from getting through.
"The purpose of this attack is to overload the service in any way possible and make it stop working or be unreachable. In this case it was not Twitter or Github that got overloaded, those services work totally fine, but a service allowing you to reach them got overloaded," Adam Surak, site reliability engineer at Algolia.com told Business Insider.
Who is responsible?
No group has taken credit for the DDoS attack yet, and Dyn says no attacker has contacted it.
The Department of Homeland Security is monitoring the attack, Politico's Eric Geller reports. The FBI is also investigating, according to Reuters.
The attack does not seem to be state-sponsored or directed, a senior US intelligence official told NBC News.
Dyn says that the attacks are "well planned and executed, coming from tens of millions of IP addresses at the same time." One of the sources of the attack is internet-connected products like printers, DVRs, and appliances, often called the "internet of things."
Code to wage DDoS attacks by hacking the internet of things was released earlier this month.
WikiLeaks says the attack is being done in support of its founder Julian Assange. Brian Krebs, a writer who was the first person to be hit with a internet of things DDoS, believes that criminals are extorting internet infrastructure companies and threatening them with DDoS.
He says that a trusted source tells him that there was "chatter in the cybercrime underground" discussing a plan to attack Dyn.
If you're having issues:
Some people online seem to think this walkthrough and Apple's support page to use OpenDNS can help mitigate the problems.
Timeline of the attacks:
Here's how the day unfolded, according to Dyn, the company being attacked.
7:10 a.m. ET:
"Starting at 11:10 UTC on October 21th-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Some customers may experience increased DNS query latency and delayed zone propagation during this time. Updates will be posted as information becomes available."
8:45 a.m. ET:
"This attack is mainly impacting US East and is impacting Managed DNS customer in this region. Our Engineers are continuing to work on mitigating this issue."
9:36 a.m. ET:
"Services have been restored to normal as of 13:20 UTC."
As of 12:06 p.m. ET, the attack had returned:
"As of 15:52 UTC, we have begun monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Our Engineers are continuing to work on mitigating this issue."
12:48 p.m. ET:
"This DDoS attack may also be impacting Dyn Managed DNS advanced services with possible delays in monitoring. Our Engineers are continuing to work on mitigating this issue."
1:53 p.m. ET:
"Our engineers continue to investigate and mitigate several attacks aimed against the Dyn Managed DNS infrastructure."
2:23 p.m. ET:
"Dyn Managed DNS advanced service monitoring is currently experiencing issues. Customers may notice incorrect probe alerts on their advanced DNS services. Our engineers continue to monitor and investigate the issue."
2:52 p.m. ET:
"At this time, the advanced service monitoring issue has been resolved. Our engineers are still investigating and mitigating the attacks on our infrastructure."
3:44 p.m. ET:
"Our engineers are continuing to investigate and mitigate several attacks aimed against the Dyn Managed DNS infrastructure."
4:37 p.m. ET:
"Our engineers continue to investigate and mitigate several attacks aimed against the Dyn Managed DNS infrastructure."
4:59 p.m. ET:
"Our engineers are continuing to investigate and mitigate several attacks aimed against the Dyn Managed DNS infrastructure."
6:20 p.m. ET:
"The incident has been resolved."
CNBC reported that Amazon investigated the issue as well, although it eventually found the issue to be with the Dyn attack. "Amazon & DynDNS investigating internet outage reports on east coast of U.S. amid reports of major websites not working properly," it tweeted.
Earlier this month, the United States transferred its oversight of DNS to an international non-profit group, a move that had been more than 20 years in the making.
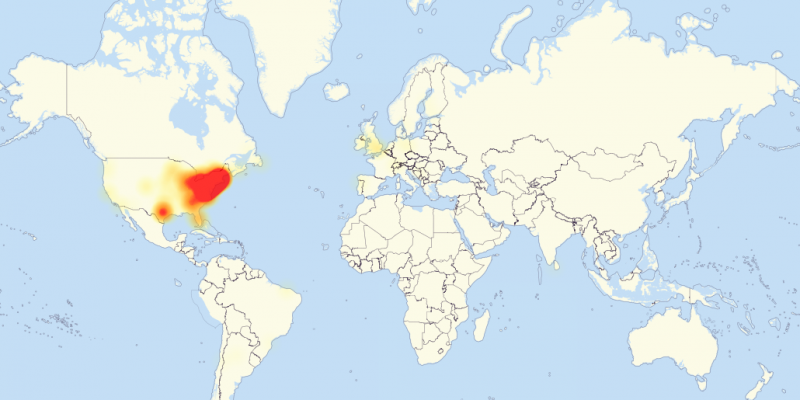
Here's a map of reported outages as of 9:20 a.m. ET, via Down Detector:
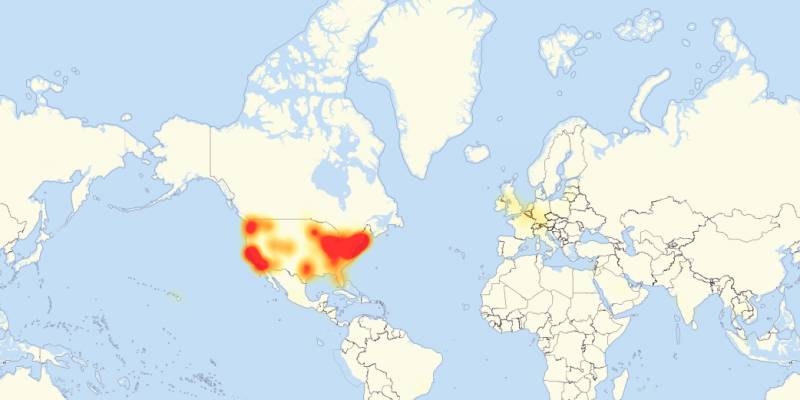
Here's a map of reported outages as of 2:16 p.m. ET:
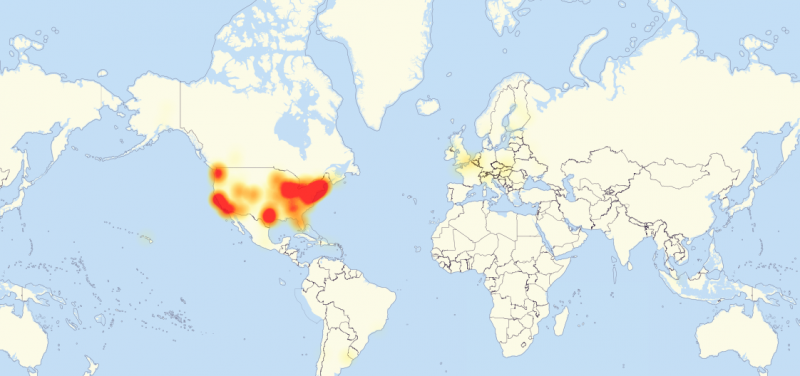
Here's a map of reported outages as of 4:58 p.m. ET:
According to Hacker News and reports, some of the sites affected include:
- DYN
- Etsy
- Github
- Soundcloud
- Spotify
- Heroku
- Pagerduty
- Shopify
- Okta
- Zendesk
- Business Insider

